Azure Security Solutions
Delivering Business Solutions
Innovation is the core of everything we do.
A cybersecurity risk assessment is a process designed to identify where your systems and security practices may be most vulnerable. The assessment includes a review of your security standards, an evaluation of your current IT controls, interviews with your team, and a risk assessment report that highlights areas of greatest concern.
How Often Should You Have a Cybersecurity Risk Assessment?
While it’s a good idea to have a process in place to continually evaluate your cybersecurity risks, a full risk assessment should also be performed once a year. Please note that this frequency may also depend on the size of your organization, your regulatory requirements, and the technology you have in place for your systems.
Cybersecurity Risk Assessment Benefits
- Identify Weaknesses:
The worst way to learn about a system’s vulnerability is through a cyberattack. By identifying your weaknesses now, you can take steps to correct them and protect your organization.
- Regulatory Compliance:
If your industry is subject to particular cybersecurity regulations, a risk assessment can help you spot areas where you may be out of compliance.
- Establish Priorities:
Knowing where you’re most vulnerable helps you to prioritize your cybersecurity efforts. An assessment helps you stay focused on the areas of greatest risk where your organization is most vulnerable.
- Better Resilience:
Cyberattacks are inevitable, but if you’ve been proactive about your security, you can ensure your organization will be more resilient. Risk assessments are a great first step.
- Stronger Security:
Regular cybersecurity risk assessments will help your organization improve your overall security posture. Over time, this virtuous cycle will make your organization stronger and stronger.
Why Your Business Needs a Cybersecurity Risk Assessment
The stakes are high: Your clients, partners, employees, and regulators all expect your organization to have adequate cyber protection. If you’re on a limited budget, how do you ensure your cybersecurity is sufficient to protect your systems and data? The answer is a cybersecurity risk assessment. By identifying the areas of greatest risk, you can make better decisions about protecting your business, both now and into the future.
How To Conduct a Cybersecurity Risk Assessment: 4 Simple Steps
- Step One: Understand Your Data
The first step in any data risk mitigation strategy is “understanding your data,” which is fundamental to every cyber security program.
What do we mean by understanding your data?
Well , people can’t steal what you don’t have, so eliminating any unnecessary data you have hanging around is super important.
To do this, you need to understand where your sensitive data is, how long you need to keep it, and who really needs to access it – often way too many people have access to data they simply don’t need.
Documenting all this is not a fun task, but eliminating the storage of unnecessary data, and restricting access to it, are two of the most basic things you can do in reducing risk.
- Step Two: Understand Your Risks
When a consultant works on a formal cyber security risk assessment, they typically draw on risk management frameworks such as the NIST cyber security framework.
NIST is a standardized security framework that was created to help improve security operations for government agencies as well as public and private organizations.
However, the NIST framework was primarily designed for large federal systems or organizations with big budgets and is unsuitable for most smaller businesses.
What you CAN do is use these frameworks to create a simplified plan, while maintaining the intent of the guidelines as much as possible, and that’s what we’re going to provide you with.
There are 3 terms you need to understand and think about before you begin this.
Threats. This can be an attacker or a hurricane. An identified threat is something that could negatively impact your business.
Vulnerabilities. This is a gap in your protection that potentially allows a threat to harm you, e.g. an unlocked door or lack of a firewall.
Risks. This is the likelihood that a threat can exploit a vulnerability. For example, an identified risk would be having the chance of having a virus infect your computer due to a lack of anti-virus software.
Now let’s move on to assessing your risks and conducting the actual risk assessment.
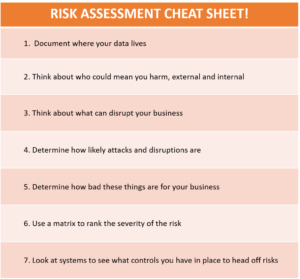
- Step Three: Security Risk Assessment Cheat Sheet
Below is a high-level cheat sheet that lists some of the most important items you need to think about when doing your risk assessment.
The answers to these questions will help you define what you need to protect, and how much you need to spend to do it.